Determine Which Dc Server Is Being Used for Authteication
In the Kerberos authentication certificate template the FQDN is in the subject field not in. By ldap389 April 24 2013 525 pm.
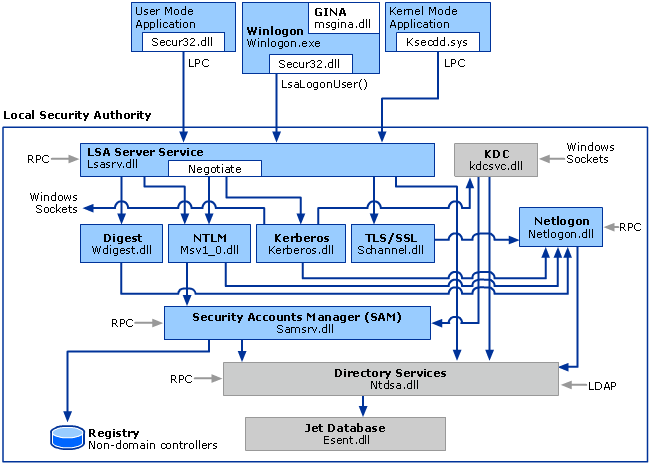
Credentials Processes In Windows Authentication Microsoft Docs
You can view the list of active Kerberos tickets to see if there is one for the service of interest eg.
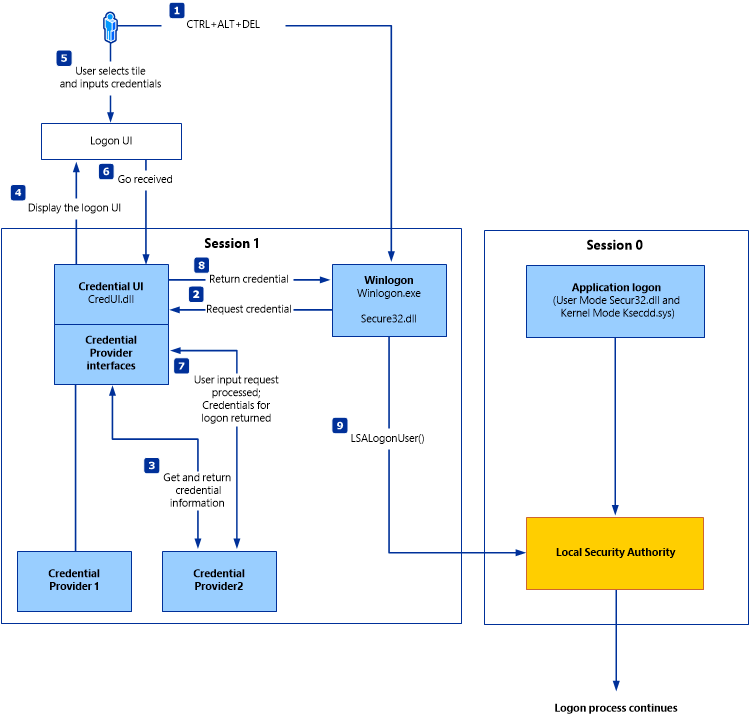
. When you run this fiddle. Hidden page that shows all messages in a thread. There are domain controllers running both Windows Server 2008 and Windows Server 2012.
To find applications that use NTLMv1 enable Logon Success Auditing on the domain controller and then look for Success auditing Event 4624 which contains information about the version of NTLM. NTLM authentication is only utilized in legacy networks. Below are the full details of the W32TM commandlet which has been the standard since Windows Vista and Windows Server 2008 and still function in Server 2012 R2.
A second way is to directly ask the manufacture of those applications to. Right click Default Domain Controllers Policy and select edit. Security is provided by encryption which requires a cipher.
You should really be auditing logon events whether the computer is a server or workstation. Type net time querysntp or. These servers are both members of the same active directory domain functional level Windows Server 2003.
SELECT ssession_id cconnect_time slogin_time slogin_name cprotocol_type cauth_scheme sHOST_NAME sprogram_name FROM sysdm_exec_sessions s JOIN sysdm_exec_connections c. Get-ExchangeServer -Identity ServerName -status fl. Specifically you can tail or cat the log file then grep for set_server_common_status to see which server was marked as working.
Show activity on this post. Refuse LM NTLM as well as the other settings listed. As you may know Exchange DSAccess will choose its list of servers based on suitability tests and then caches this access info.
In an AD infrastructure the root is defined by dc organizational unit is defined with ou and the container or user group are defined by cn. Most of the authentication are using Kerberos. To get the current list of DCs and GCs run the following PowerShell command.
Large netmon cap may be. TLS Transport Layer Security and SSL Secure Sockets Layer are protocols that provide data encryption and authentication between applications and servers where the data is being sent across the network An HTTPS script uses either SSL or TLS for the transport layer. The following approach follows the specification and currently only works in Firefox because Chrome implements getStats incorrectly at the moment.
The Kerberos Authentication certificate Template has Domain name in the SAN field in order to allow strong KDC validation. NT LAN Manager NTLM is the default authentication scheme used by the WinLogon process. Created before we can found something out of it.
Vasconf realms section after the failed DC. This restricts the LDAP server. Hopefully a version of the adapterjs polyfill should be available soon that will make this work in Chrome as well.
Hi I have 3 x ZCM 1123a primary servers Win 2008R2 VM Win2008R2 physical SLES11 physical with about 1600 max devices connecting. UDP 137 - UDP 137 NetBIOS Name UDP 138 - UDP 138 NetBIOS Netlogon and Browsing 1024-65535TCP - TCP 139 NetBIOS Session. If the Domain Controller DC goes offline Authentication Services will automatically failover to another available DC.
Theres also a way to log Kerberos events if you hack the registry. Type w32tm query status. Ive updated the example to follow the latest spec with maplike getStats.
These web sites use windows authentication with only the NTLM option specified no Kerberos. Forms-based authentication over proper validated TLS is the modern way forward for web application authentication that require non-SSO Single Sign On capabilities eg SAML OpenID OAuth2 FIDO et al. Please try to use the following query.
Microsoft no longer turns it on by default since IIS 7. You may also be interested in our article on how to set an authoritative time server. Log on again then sudo tail -n 20 varlogsssdsssd_mydomainlocaldomainlog where mydomainlocaldomain is the FQDN for Active Directory.
The server FQDN name has to be in the SAN field or in the Subject field for LDAPs to work. Now I can go select Computer Configuration Policies Windows Settings Security Settings Local Policies Security Options as shown in Your link Then I can set LAN Manager authentication level to Send NTLMv2 response only. Tell if they are using NTLM or NTLMv2.
A protocol that is used when a user attempts to access a secure Web server. The third way is to use netmon to capture the packets if possible since. Enterprise security using ClearPass Policy Management ClearPass Security Exchange IntroSpect VIA 360 Security Exchange Extensions and Policy Enforcement Firewall PEF.
When Authentication Services needs to connect to a new DC it examines the DCs it knows about and selects an available DC using the following. It is also the default method of network authentication for services. A protocol that is used with either a password or a smart card for interactive logon.
I want to get the initial. It uses three ports between the client and domain controller DC. Command replace ServerName with a valid Exchange server name below.
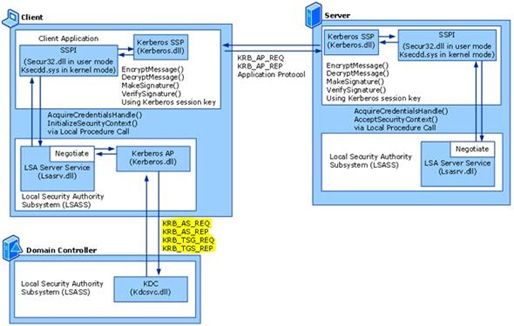
Understanding Read Only Domain Controller Authentication Microsoft Tech Community

Credentials Processes In Windows Authentication Microsoft Docs
Active Directory Authentication
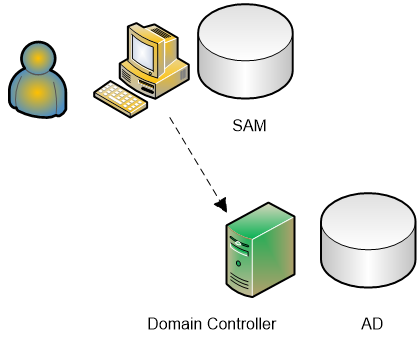
Chapter 3 Understanding Authentication And Logon
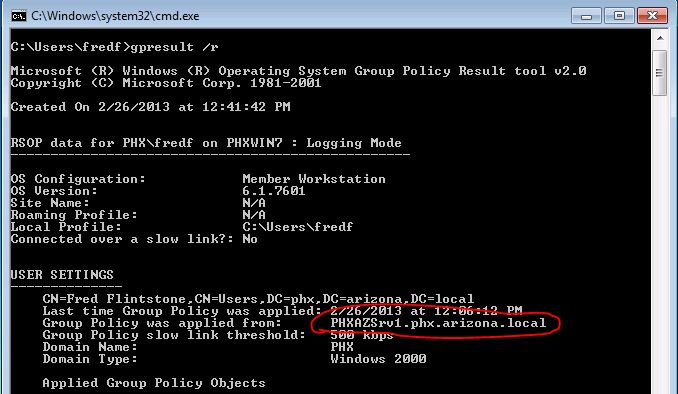
Windows Server How To Identify Which Domain Controller Authenticated A User Interface Technical Training
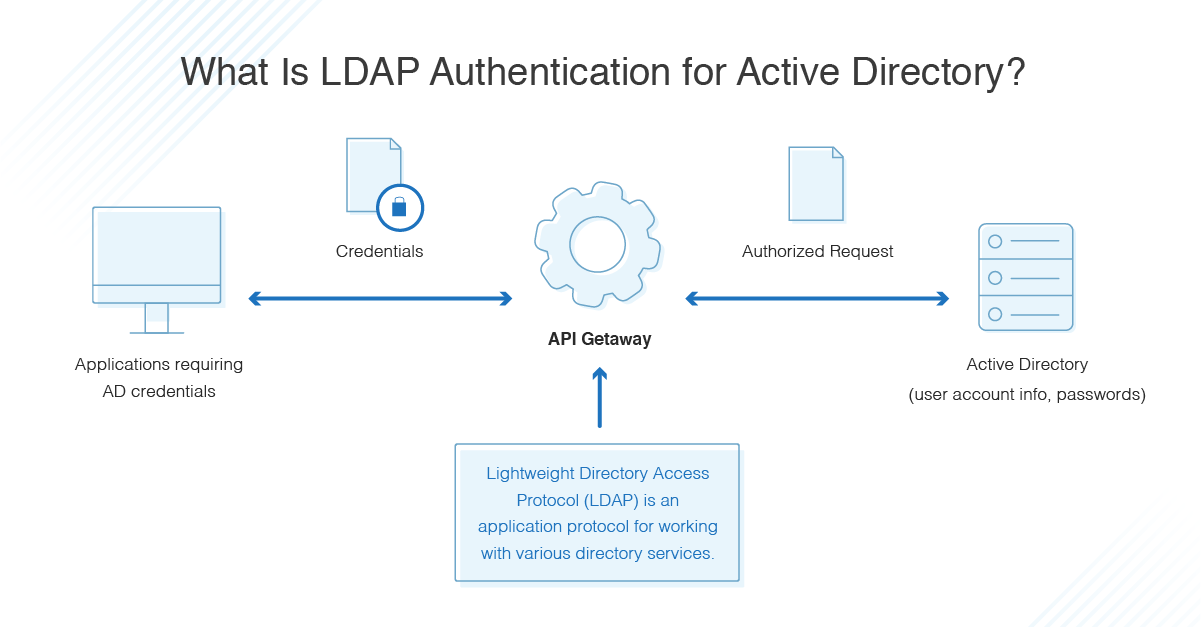
Active Directory And Ldap Authentication Guide Dnsstuff

Servers Com Services In 2021 Web Panel Health Check Private Network

How To Find Which Dc A Computer Is Authenticated To
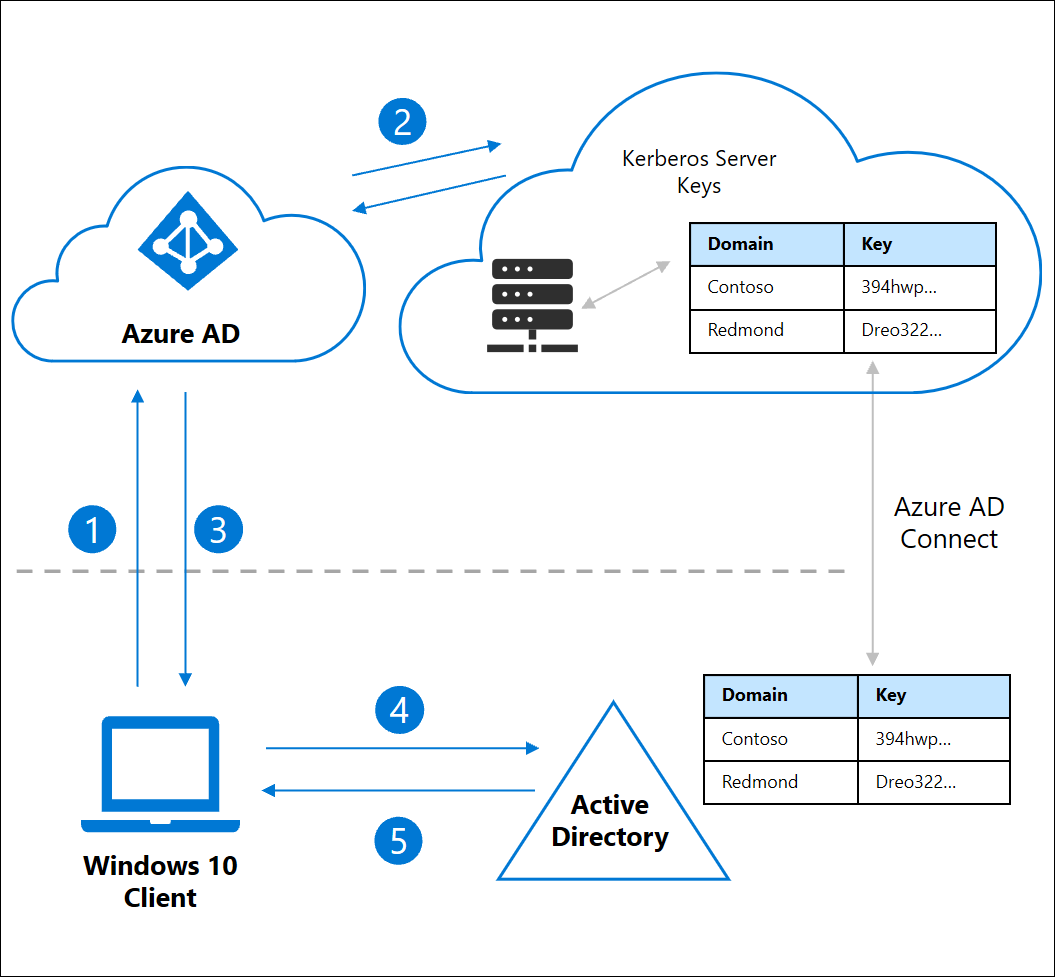
Passwordless Security Key Sign In To On Premises Resources Azure Active Directory Microsoft Docs
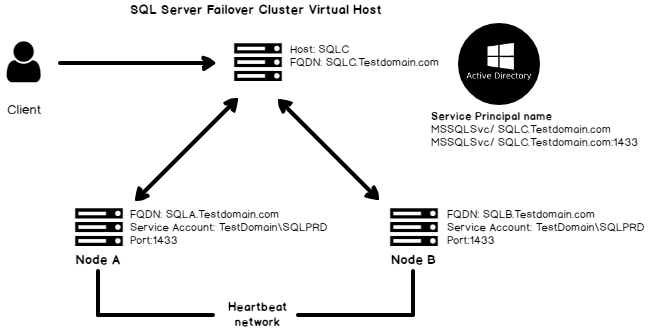
Overview Of Service Principal Name And Kerberos Authentication In Sql Server

Credentials Processes In Windows Authentication Microsoft Docs
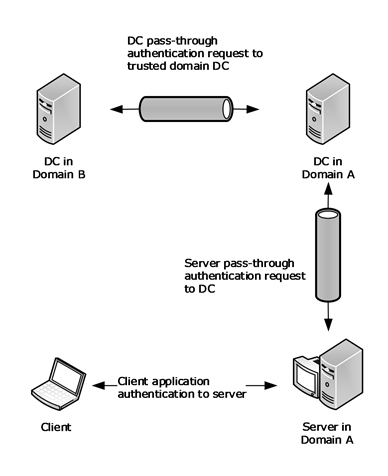
Ms Nrpc Pass Through Authentication And Domain Trusts Microsoft Docs
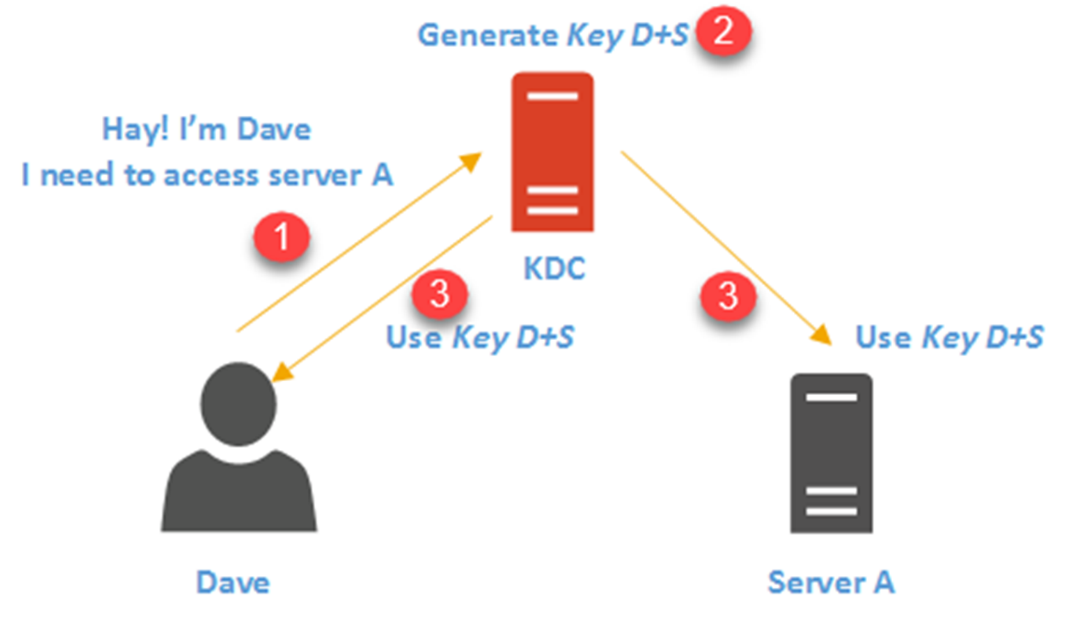
How Active Directory Authentication Works Technical Blog Rebeladmin
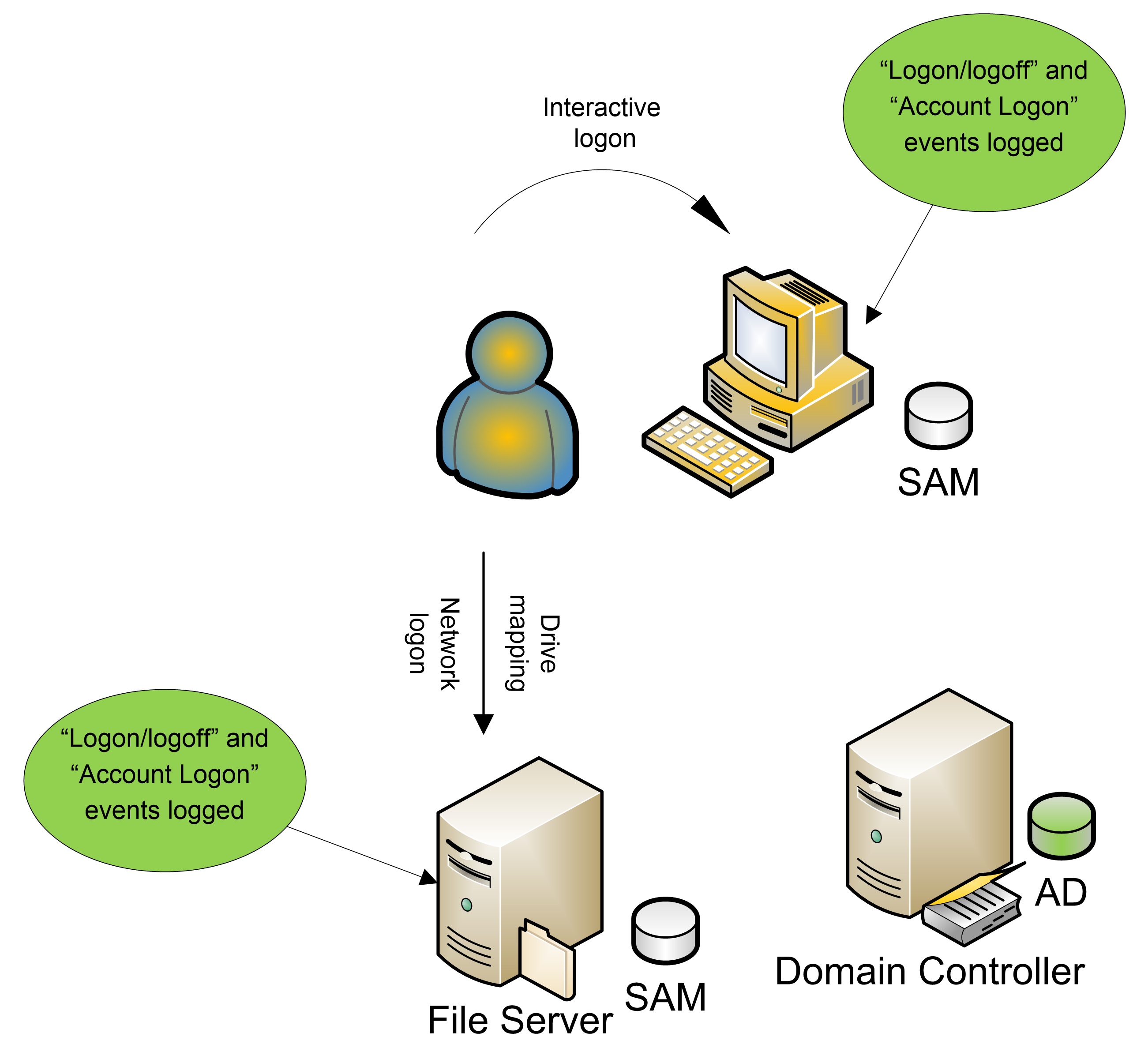
Chapter 3 Understanding Authentication And Logon
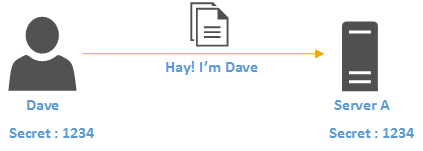
How Active Directory Authentication Works Technical Blog Rebeladmin
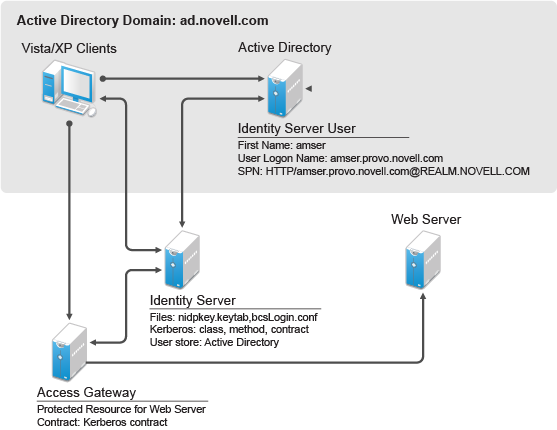
Kerberos Authentication Access Manager 4 5 Administration Guide
2 2 User Authentication Softether Vpn Project

Setting Up Radius Server Wireless Authentication In Windows Server 2012 R2 Techbast
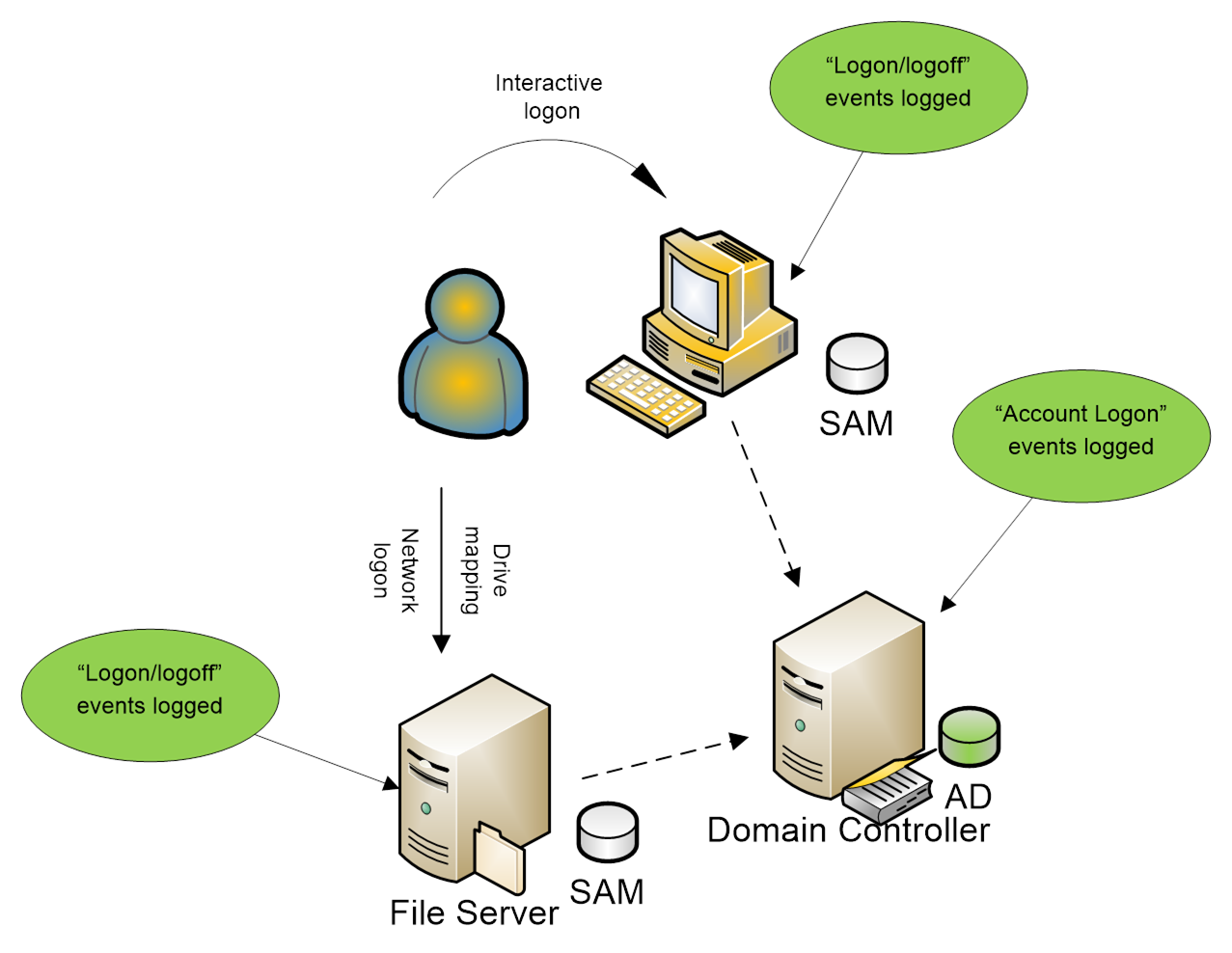
Comments
Post a Comment